netcup wiki
General

Phishing Protection
Phishing affects numerous companies in various industries, including internet service providers like netcup. With the aim of taking over customer accounts, criminals try to obtain access data. How can you recognize this and protect yourself against it? In the following we give various tips.
Phishing is a technique used by criminals to gain access to customer accounts of others, e.g. from netcup. These are then misused for various purposes. Phishing uses fake emails to trick the recipient into entering login details on a spoofed website. The data does not end up with the company the site is modeled after, but with the criminals and can then be misused for various purposes.
Sometimes phishing emails also contain attachments (e.g. alleged invoices) that are infected with malware, with the aim of compromising your computer and causing further damage.
Netcup is currently affected by various phishing waves. In this article we want to give you information on how to protect yourself against such fraud attempts.
What is netcup doing to prevent the sending of phishing emails in their name?
Like many large companies, netcup is affected by phishing campaigns. Criminals are trying to gain access to customer data from netcup customers. In some cases, techniques are even specifically targeted to contact only netcup customers: For example, lists of domains are searched. It is then checked whether the domain is actually hosted by netcup and only in this case such an email is sent.
Netcup uses techniques (e.g. SPF) on its domain netcup.de to prevent so-called mail spoofing, i.e. forging the sender address of emails, as much as possible. However, this is not a complete guarantee to prevent such forged senders for all recipients.
If netcup receives reports of phishing emails, we take various steps to stop sending as quickly as possible and avoid further damage: We contact the sender provider and ask them to block the sender. We also enter the URL of the spoofed website on numerous phishing blocklists so that browsers warn when the corresponding website is accessed after some time. However, it usually takes several hours to days for these warnings to be checked and activated. Therefore, potential victims should not rely on such protective measures.
We inform our customers in various ways: For example, through articles like this one, in the event of acute phishing campaigns known to us, through a banner on our website and through a status message on netcup-status.de. However, phishing campaigns can take place at any time and the lack of such a warning does not mean that no phishing emails are currently being sent.
We cannot completely prevent the sending of such messages in principle. Therefore, it is important that you know how to recognize a phishing email and how to behave correctly when you receive one.
How do I recognize a phishing email?
Phishing emails are modeled on real emails from netcup, sometimes more and sometimes less credibly. But there are several ways to recognize this type of email.
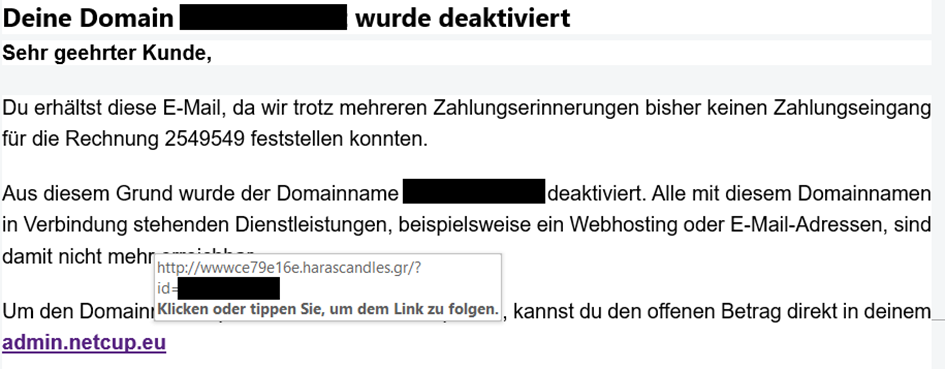
Hover your mouse over the displayed link in the email that allegedly leads you to a netcup panel. The actual destination of the link, which is usually then displayed in the bottom left of your email program / web browser, may differ from the text displayed in the email. The link does not point to a netcup Homepage, but either to a completely different website or to a similar looking URL that is designed to deceive you. If you are unsure whether the link actually points to a netcup Homepage, it is better to call up the page manually via the URLs already known to you, not via the link in the email. For example, if you receive an alleged invoice, you can also log into the Customer Control Panel (CCP) manually and retrieve it. Do not follow the link contained in the email.
Example:
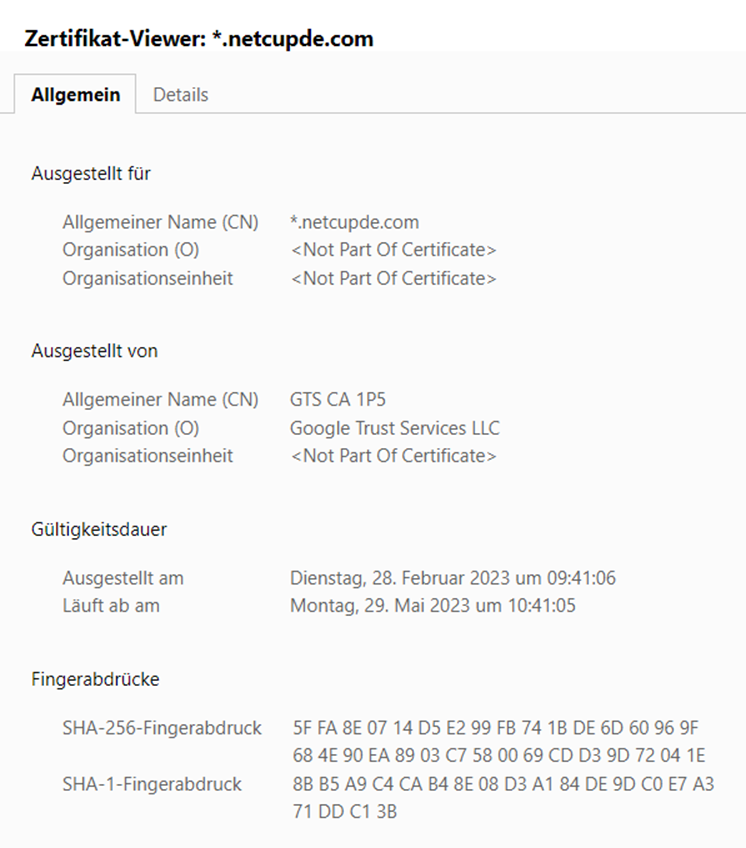
It has often been falsely spread that links starting with "https://" are particularly secure. But this is not the case. Criminals can also obtain SSL certificates for their websites. So this is not a criterion for determining the security of a website.
Example:
Phishing emails are often (but not always) provided with questionable spelling, grammar, punctuation and wording. However, there are also phishing emails that can look deceptively authentic in this regard.
Corresponding messages often try to put pressure on. For example, they often point out the consequences of inaction and even threaten directly, e.g. with blocking / deleting your domains or your tariffs with us. The aim of the criminals is to put you under pressure and prompt you to act quickly and thoughtlessly. Treat emails, even if they seem urgent, always with a certain skepticism, especially if they directly or indirectly prompt you to log in to a website.
Example:
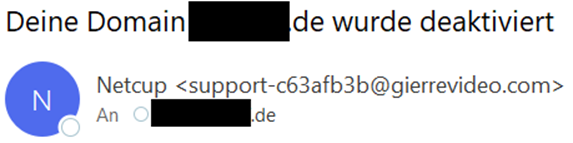
The sender email address of phishing emails often does not match the usual sender address of legitimate messages from netcup. All messages sent by netcup are sent from an email address ending in "@netcup.de", netcup newsletters are also sent from an email address ending in "@netcup.news". However, depending on the configuration of the receiving email server, the sender address can be forged. Therefore, this cannot be used as an unambiguous criterion. Sender email addresses can basically be forged. Please also note that an email sender consists of two parts: the displayed sender name (e.g. "netcup GmbH") and the sender email address. The sender name can be set freely in any case and will therefore usually contain "netcup" in a professional phishing email and can therefore only be distinguished with difficulty from a real email from us.
Example:
Also check the recipient address. If the email was sent to an email address that is not stored anywhere with us, it is quite likely that it is not a legitimate message, since in that case it would not even be known to us.
Phishing emails often contain an incorrect salutation, i.e. your name is not given or not given correctly. However, it is also possible that the criminals have obtained your name through other means. Therefore, this is not an unambiguous characteristic of a phishing email, but can at least be an indication.
Do not open any attachments if you have doubts about the legitimacy of an email message. Netcup only sends invoices with the file extension ".pdf" as a matter of principle. Sometimes users are also misled by double file extensions: e.g. ".pdf.exe" - this is an executable file, not a PDF. If you have any doubts, you can find all invoices in your Customer Control Panel (CCP) as well. Call this up manually, not via a link contained in the email.
Keep your operating system and all programs used up to date with updates. In particular, the operating system used, your web browser, your email program, and your PDF reader play an important role here.
Activate two-factor authentication offered in the CCP and additionally security mode in the Server Control Panel (SCP) if you use it. To then access your accounts with us, the attackers need the second factor. Access will be made much more difficult for them or even impossible.
Use different passwords for each service: Otherwise, attackers can compromise your accounts with other providers by obtaining the login details for one account. To make this easier for you, the use of a password manager is recommended.
In case of doubt, we recommend contacting our support. Our support can confirm whether an email allegedly sent by us is legitimate or not. Do not reply directly to the email, but write to us manually, preferably via an email to mail@netcup.de. We are also happy to receive your information regarding phishing emails so that we can take action as quickly as possible and warn our customers.
I received and recognized a phishing email. How do I proceed?
Please do not open any links contained in the email. Do not open any attachments either. A criminal who wants to prompt you to enter your login details on a spoofed website would certainly have no scruples about infecting you with malware if possible. We advise you to inform us about the email by forwarding the email including the header to abuse@netcup.de. Please note that we cannot process the email without the header. Please send us the email exclusively including the header. Email programs usually offer an option to display the "source text" of the message. You can also save the email as an .eml file and send it to us as an attachment with a short explanation. This allows us to examine the message and take protective measures for our customers.
What if I suspect I have already fallen for a phishing email?
If you have fallen for a phishing email, log into your Customer Control Panel (CCP) and any other accounts obtained through us (e.g. Server Control Panel) immediately and change your password. Check your computer for malware with an up-to-date antivirus program. Contact our support by email at mail@netcup.de with all available information. Send the spoofed email ideally with, as described in the previous section, and explicitly point out that you have already submitted your login details via the spoofed website.