netcup wiki
General

Phishing
1. What Is Phishing?
Phishing is a form of social engineering that tricks people into revealing confidential information or performing certain actions. Someone pretending to be from a trustworthy institution or person contacts one or more people by email, phone, or text message. The goal is to obtain sensitive data, such as personal information, bank and credit card details, and passwords, or to trick people into downloading malware.
The attackers pretend to be reputable companies, authority figures, friends, or acquaintances. The targets receive a message from the attackers asking them, for example, to log into their account, pay a bill, click on a link, or open an attachment.
How Do Attackers Obtain Their Data?
Waves of phishing have repeatedly affected netcup. However, this does not mean that netcup has been hacked or that there has been a data leak on our side.
Scammers have many ways to obtain their victims' contact information:
- Purchasing data sets on the dark web.
- Publicly available email addresses on social media.
- Sending to frequently used email combinations such as "mail@" or "contact@."
- Email harvesting (automatically searching the internet for addresses).
- Malware that reads information from email programs and browsers and collects addresses.
The attackers also try to obtain sensitive customer data by using techniques specifically designed to contact netcup customers. They use publicly available information to check whether a domain refers to a netcup IP address. If so, they send a phishing email. Domains are publicly accessible in various sources, such as search engines or rDNS/PTR entries of IP addresses. Additionally, every domain for which an SSL certificate has been requested – which is the case for the majority of domains today – appears in Certificate Transparency Logs.
Systems infected with malware that have sent messages to affected email addresses in the past can also be sources of such domains or addresses.
We cannot prevent these emails from being sent or stop them entirely, as we are also targets of these criminals. We rely on cooperation with the sending providers for prevention and resolution. Therefore, we advise you to remain vigilant at all times to protect yourself from such attempts at fraud.
2. How Do I Recognize Phishing Emails?
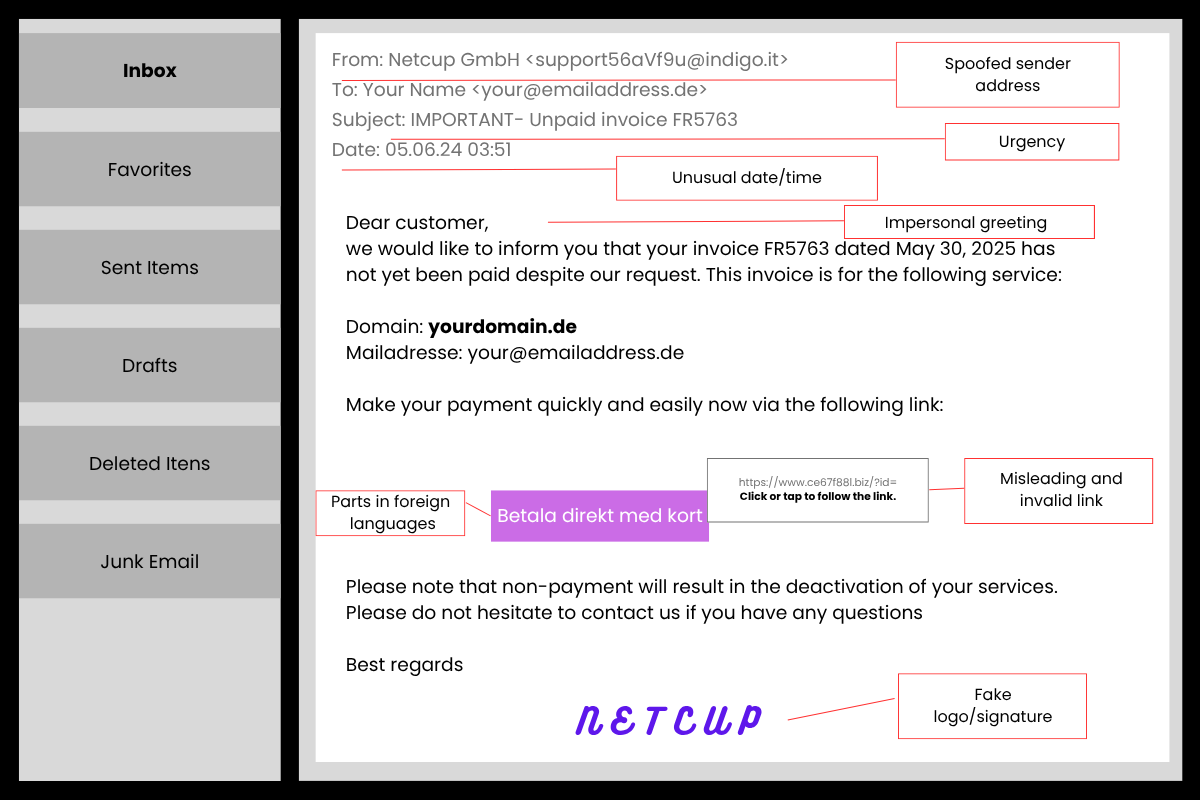
Phishing emails often resemble real messages from banks, online shops, or companies. However, they usually contain obvious features that make them easy to recognize.
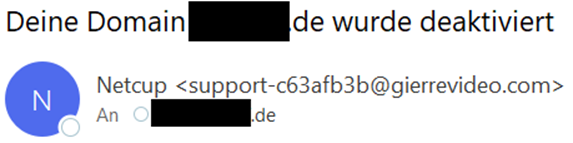
1. Check the Sender – Is the Email Genuine?
Do you recognize the email address? Note that an email sender consists of 2 parts: the displayed sender name (e.g., "netcup GmbH") and the sender email address. The displayed sender name can be chosen freely and can imitate the names of other people or companies. The Carbon Copy (CC) field shows whether the email was also sent to other people.
Also check the recipient address. Was the email sent to an address that you did not register with netcup? If so, it is very likely that the message is fake.

All messages from netcup are sent from email addresses with the following ending:
- @netcup.de
- @netcup.news (Newsletter)
- @registrant-verification.com (Stripe verfication)
2. Pay Attention to the Language – Are You Being Addressed Correctly?
Spelling and grammar errors are common in phishing messages and often serve as warning signs. However, the use of artificial intelligence and automatic text generation are making it easier than ever for scammers to create deceptively genuine, and almost error-free messages.
Entire messages or sections of text written in a foreign language may also indicate that a message is a scam.
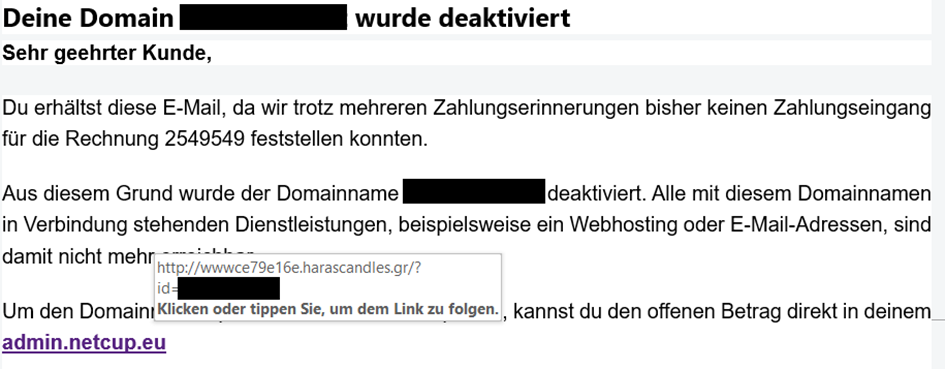
Also pay attention to how the message is addressing you: Does the message begin with a generic greeting, such as "Dear Sir or Madam," "Hello," or "Dear Customer"? Is your name spelled correctly? Errors or inconsistencies in the greeting can indicate a phishing email.
3. Check Links – Where Do They Really Lead?
If an email contains a link to another website, verify that it leads to the official website. To do so, simply hover your mouse over the link in the email. This will show you the URL that the link actually leads to. If you are unsure whether the link leads to the company's official website, it is better to access the page manually using the URL you already know. Additionally, never enter login details on websites that were opened via a link in an email.

There is a widespread misconception that links beginning with "https://" are particularly secure. However, this is not true. Criminals can obtain SSL certificates for their websites, too. Therefore, this factor alone is not an adequate criterion for determining the security of a website.
4. Do Not Open Attachments if You Are Unsure
Do not open email attachments if you have doubts about their legitimacy. Attackers use with misleading file extensions (e.g., "pdf.exe") in file attachments to hide malware. If you are unsure whether an attachment is an invoice or a legitimate document, open it directly from your user account.

Invoices from netcup always have the file extension ".pdf". If in doubt, access your invoices via the Customer Control Panel (CCP).
5. Beware of Threats – Is the Message Trying to Pressure You?
Phishing messages often try to create a sense of urgency. Attackers often point out the consequences of inaction and make threats such as, "Act now, otherwise..." or "Your account will be blocked!". Their aim is to pressure you into taking quick, impulsive action.
In such situations, remain calm and always treat these messages with a certain degree of skepticism. Ask yourself: Did you expect this email? And does it even make sense?

If you have any doubts, contact Customer Support. Our team can verify the legitimacy of any email supposedly sent by us.
3. I Have Received and Recognized a Phishing Email. What Should I Do?
Do not open any links or attachments in the email. It is best to inform us directly about the phishing attempt.
Send the email, including the header, to abuse@netcup.de. We cannot process emails without headers. Click here to learn how to view the header: Viewing Email Headers. Alternatively, you can save the email as an .eml file and send it to us as an attachment with a brief explanation.
Tips for Better Cybersecurity
-
Keep your operating system and all of your programs up to date. Pay particular attention to your operating system, web browser, email program, and PDF reader.
-
Make sure that your device is protected by a suitable antivirus software.
-
Use a different password for each service. Otherwise, attackers can compromise several of your accounts by obtaining a single password. We recommend using a password manager.
- If possible, activate two-factor authentication (2FA). This makes it significantly more difficult for attackers to access your account because they will need the second factor. For your netcup account, you can activate 2FA in the Customer Control Panel (CCP). If you use a server from netcup, also activate security mode in the Server Control Panel (SCP). This will prevent direct login to the SCP. For netcup web hosting, you can activate 2FA in the Webhosting Control Panel (WCP) under Account > My Profile.
- Always be vigilant and do not trust messages from unknown senders or with untrustworthy content. Do not automatically trust a well-designed website.
It may look exactly like the original, but it could contain false links and errors, making it a scam. If you frequently visit the page mentioned in the message, add it to your favorites or open it directly via your browser instead of clicking on a link.
4. What Should I Do if I Suspect That I Have Already Fallen for a Phishing Trap?
If you suspect that you have already interacted with a fraudulent message, proceed as follows:
-
Immediately log in to the affected accounts (CCP, SCP, WCP) and change your password.
-
Scan your computer for malware using an up-to-date antivirus software.
-
If you have made payments or provided payment information, contact your bank immediately.
5. What Is netcup Doing to Combat Phishing?
We cannot completely prevent phishing emails from being sent. However, if we receive reports of such emails, we will take various steps to stop them from being sent as quickly as possible and prevent further damage.
-
We contact the sender's provider and request that they be blocked.
-
We block the corresponding IP addresses from receiving emails on our mail servers.
-
We add the URL of the fake website to numerous phishing block lists so that, after a certain amount of time, browsers will warn you when you visit the website in question. However, it usually takes several hours to a few days for these warnings to be verified and activated. Therefore, if you are potentially affected, you should not rely on these protective measures.
Our systems use a combination of technical checks (e.g., SPF, DKIM, DMARC), reputation databases, and learning spam filters. These are continuously adapted and improved. This allows us to prevent mail spoofing, i.e. the falsification of the sender address of emails, as much as possible. However, we cannot guarantee that fake senders will be blocked for all recipients.
You can check at any time whether netcup is currently affected by a phishing wave at https://www.netcup-status.de/. Please note that phishing can occur at any time. The absence of a status message does not mean that phishing emails are not currently being sent.